Devices
Analyze devices
On the Devices page, you can quickly analyze enrolled devices for misconfigurations and vulnerabilities, such as firewalls that aren't enabled. You can also add or manage devices from this page.
In order to see devices, you must first enroll the device by adding a Device360 credential to the latest Beyond Identity Authenticator (minimum version 2.94 or later). Note that this is a different passkey than the one used for the Beyond Identity console and passwordless authentication.
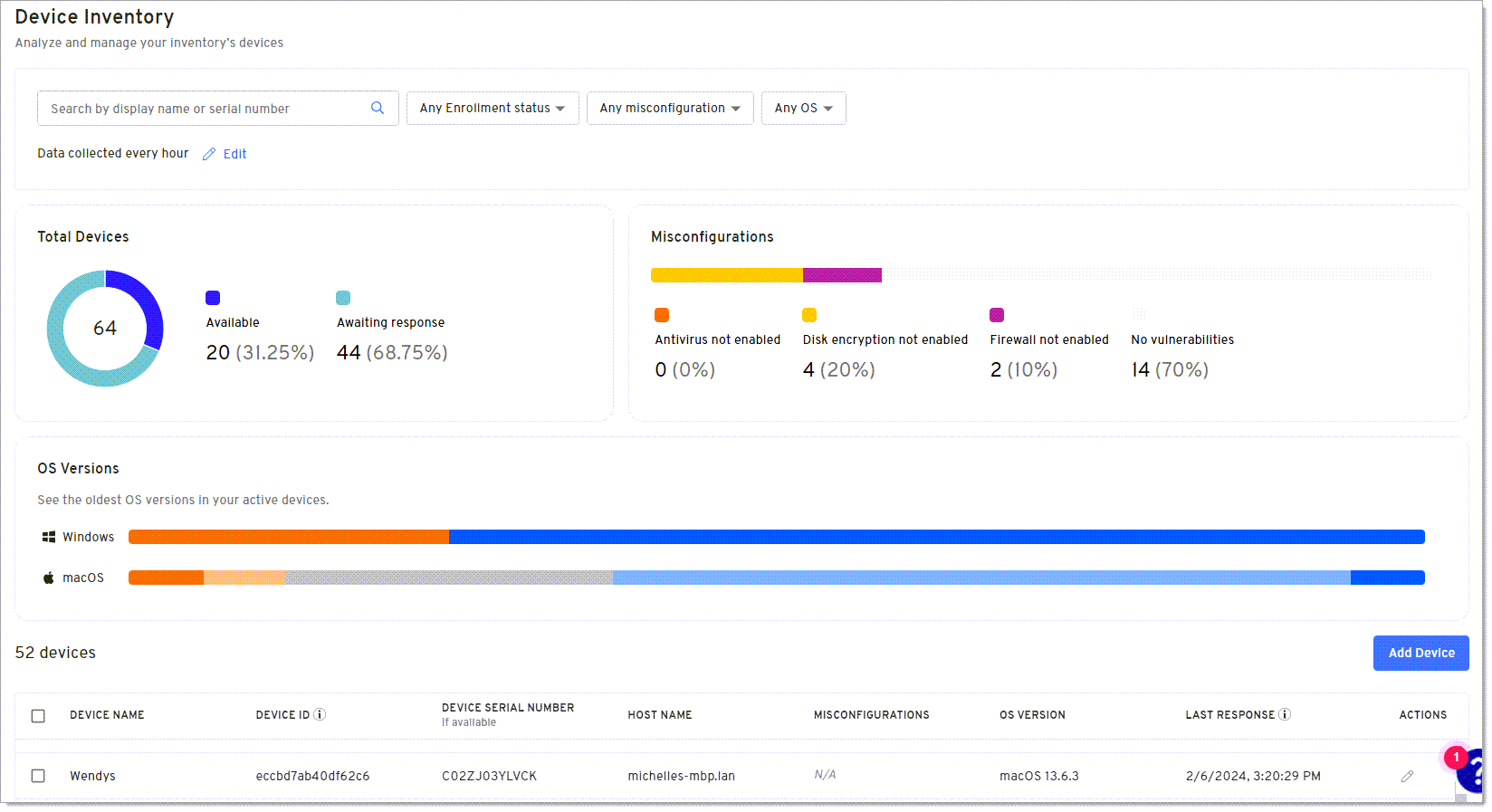
Search for a device
Use the Search bar to quickly find a device when you know the display name or serial number.
-
Select either Display name or Serial number in the Search field.
-
Press Enter on the keyboard or click the Search icon. The graphs and table update to display the search results.
You can click x in the Search bar to clear the results.
View the enrollment status for devices
You can use the filter above the graphs or select an option in the Total Devices widget to quickly locate devices that haven't yet added the enrollment code to begin collecting data or to find the date and time a query last ran on devices that are enrolled.
Available options are:
-
Active - Date and time of the last response for a query.
-
Pending - Device is not yet enrolled.
noteThe enrollment code expires after 10 minutes so you may need to generate a new code for the device.
Selecting an enrollment status will update the remaining graphs on the page and the Devices table with your results.
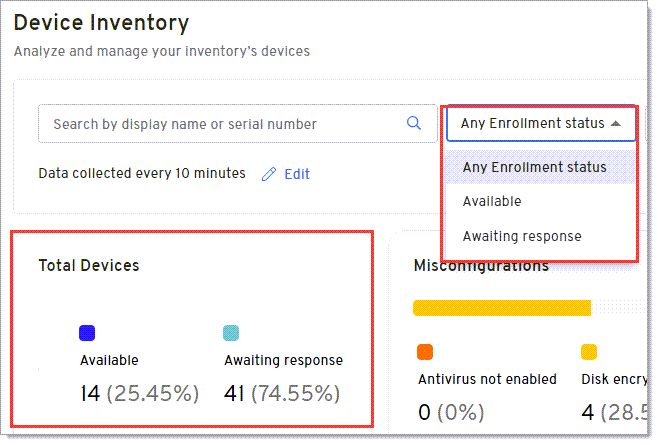
View misconfigurations for devices
You can use the filter above the graphs or select an option in the Misconfigurations graph to view devices that contain common misconfigurations that lead to vulnerabilities. This helps you to quickly prioritize and fix misconfigurations before they become a problem.
-
Select a misconfiguration option from the Any misconfiguration drop down to update the graphs and Devices table with your results. The drop down only shows misconfiguration options that exist for enrolled devices. For example, in the image above, there aren't any devices where the Antivirus and Firewall aren't enabled so those options don't appear in the current list.
or
-
Click a misconfiguration option from the Misconfigurations graph to update the remaining graphs on the page and the Devices table with your results.
You can take a screenshot of the initial graphs and then take screenshots of the graphs over time to show progress to the executive team and stakeholders as you remediate the misconfigurations and reduce potential risks to your organization.
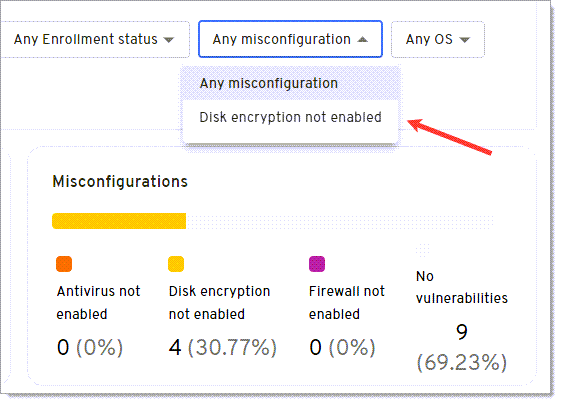
View OS Versions
You can use the Any OS filter above the graphs or select an option in the OS Versions graph to identify devices on older and more vulnerable operating systems.
-
Select an operating system from the Any OS drop down to update the graphs and Devices table with your results. If you prefer to filter by a specific OS version, use the graph option below.
or
-
Hover over different color sections for an operating system in the OS Versions graph and click that version to update the remaining graphs on the page and the Devices table with your results.
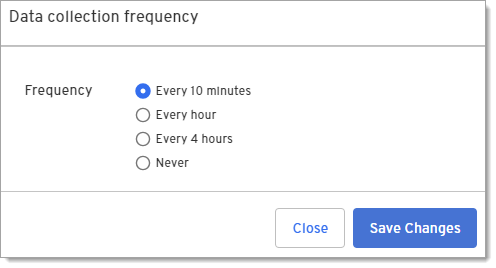
Update the data collection interval
You can specify the interval for how often device attributes in the table on this page will be collected from devices that are online.
-
Click Devices in the navigation pane.
-
Click Edit beside Data collected every x.
-
Under Frequency, select how often you want Device360 to poll enrolled devices and return results that display in the Devices table.
-
Click Save Changes.
Devices table
The Devices table shows device details and vulnerabilities from polling the device based on the data collection setting.
You can click a device row to view details for that device.
| Column | Description |
|---|---|
| Device Name | A custom name you can set for the device by clicking Add Device on this page. If you don't add a device name, the entry will be blank on this page and will show as "Not Available" for device query results. |
| Device ID | The Device ID is a value assigned by Beyond Identity and is useful to:
|
| Device Serial Number | The serial number associated with the device. |
| Host Name | The label assigned to the device on network. |
| Misconfigurations | Displays any misconfigurations found on the device that can cause vulnerabilities, such as a firewall that isn't enabled so you can begin remediation. |
| OS Version | Displays the operating system version of the device. Use this column to locate devices that are on vulnerable operating systems. |
| Last Response | The last time the authenticator responded to a device query. Available values are:
|
| Actions | Click the Edit icon to perform the following:
|
Rename devices
You can add a name for a device or rename a device on the Devices page. If you don't add a name, the Device Name on the Devices page will be blank and the Device Name for any query results will display as "Not Available".
-
Click the Edit icon under the Actions column on the Devices page.
-
Enter or update the name in the Device Name field.
-
Click Save changes.
Rebind devices
You can rebind or re-enroll a device by generating a new enrollment code and adding it to the Beyond Identity authenticator.
If you are a Secure Workforce customer, this will not impact the passkey in the authenticator that allows you to securely sign into corporate applications without passwords.
-
Click the Edit icon under the Actions column on the Devices page.
-
Click Generate new enrollment code.
-
Copy the Enrollment code.
-
Click Save changes.
-
Remove the current passkey from the authenticator. For more information, see Remove passkeys from devices below.
-
Add the regenerated enrollment code to bind your device to this tenant:
a. Click the + button to add the new enrollment code.
b. Paste or type the enrollment code in the Enter 9-digit code screen. Note that a cursor doesn't appear on the screen.
The device will be added to the Device table with a status of Pending until internal queries complete. Once those complete, the status will change to Active. For more information, see Analyze devices above.
Remove passkeys from devices
You may need to remove the device credential from a device when rebinding a device
-
Open the Beyond Identity authenticator and select the passkey you want to remove.
-
Click About this passkey.
-
Click Remove passkey from computer.
Delete devices
This will not delete the passkey from the authenticator that allows users to securely sign into corporate applications without passwords.
-
Click the Edit icon under the Actions column on the Devices page.
-
Click Delete Device. A message displays that the device was successfully deleted and the device is removed from the Device table.